Android, malicious app downloaded millions of times on Google Play Store
Symantec has found 25 applications with malware on Android, capable of deleting its own icon from the device’s Home page and fraudulently advertising it.
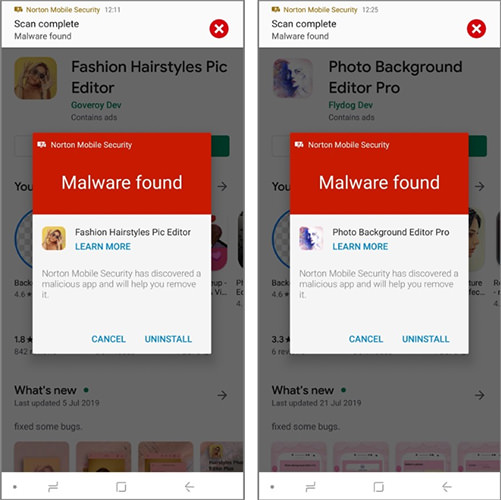
Two security researchers from Symantec Threat Intelligence, May Ying and Martin Zhang, discovered and reported to Google 25 Android apps with malware available on the Google Play Store.
Altogether, the reported apps have been downloaded 2.1 million times, and all share a similar structure with regards to the written code to avoid the automatic detection of the malware used on the Android store.
The apps reported by Symantec have been published under the name of 22 different developers, and have been uploaded to the store all in the last 5 months. The similarities in the code suggest that at the base of software with malware there is only one organization, the interest in spreading the malicious code. It is specifically an adware, or a code designed to spread advertising on the device in use.
Once installed the apps begin to send advertising on the screen even when the apps are closed, and they begin to do so wisely only after some time from the installation. At the time of writing, the 25 discovered applications have been removed from the Google Play Store, there is the possibility that other apps with the same code are present on the Store or may be uploaded bypassing Google’s screening.
25 apps with malware on Google Play Store and Android
Many of the incriminating apps were linked to the worlds of photo editing or fashion. One of these was a sort of clone of a legitimate ” photo blur ” app, published by the same developer, and present among the Google Play Store trends: ” We believe that the developer has voluntarily developed a malicious copy of the famous app hoping that some users download the malicious variant “, Symantec specifies.
On a technical level, the apps behave normally after the first installation but as soon as they are launched, they download a remote configuration file that includes the malicious code. The keywords associated with the fraudulent activity, including a specific code to hide the icon on the mobile Home, are protected by encryption.
Once the file is downloaded, the app gets the details to send full-screen advertisements to the terminal, with the aim – of course – to fraudulently generate revenue from displaying the banners.
” Thanks to the ability to hide apps from the smartphone’s home, users easily forget they have downloaded them, ” the researchers point out, and without a way to link the banners to a specific app, the developers had the go-ahead to send banner ads without that the victims could not even suspect the real origin.