Checkpoint discovers a vulnerability in the OTA protocol that puts Android smartphones at risk
The problem affects the smartphones produced by Samsung, Huawei, LG and Sony, but it seems that the most vulnerable to this type of attack are the Samsung devices, which incidentally are among the most widespread on the market.
Check Point Software Technologies researchers have discovered a new way to carry out an SMS Phishing attack against Android smartphone owners. An attacker can easily manage to convince a user to accept new phone settings, thus allowing the scammer to redirect all the device’s Internet traffic through a proxy that he has control over.
The OMA CP protocol is vulnerable, but Sony refuses to accept it
The OTA (Over The Air) settings update functions are extremely convenient and allow telephone operators to easily configure their customers’ phones via a trivial SMS. The standard currently used by the industry for this type of updates is the OMA CP (Open Mobile Alliance Client Provisioning) which carries with it a serious problem: for a user, it is very difficult to understand if the settings update has been sent lawfully by operator or a scammer.
The flaw is quite serious but fortunately Samsung and LG have already published a fix. Huawei will publish it shortly while Sony, the only voice outside the choir, refuses to accept the problem, stating that its devices follow the OMA CP specifications.
How can this type of attack be launched?
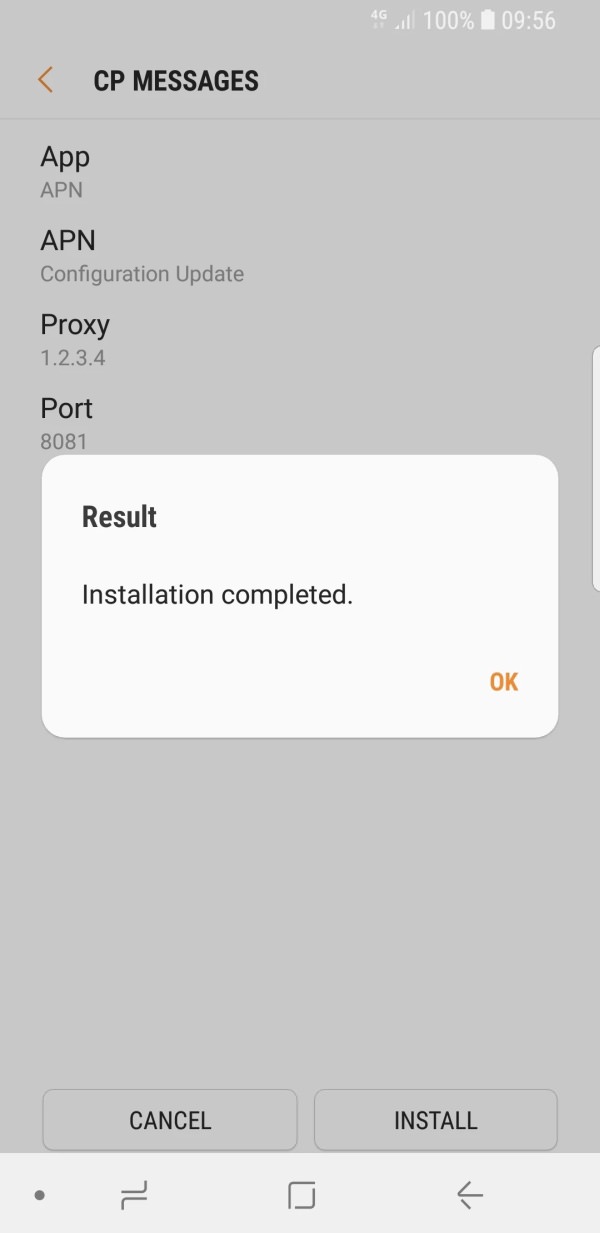
The vulnerability is rather simple to exploit. A striker just needs to have a cheap GSM modem (there are USB models that cost less than 20 euros) and create a small script to compose a message compatible with the OMA CP standard containing the following information: MMS message server, proxy address, homepage and proxy bookmark, mail server, Directory server to synchronize contact and calendars.
The message will then be sent via the modem to a specific user or if you prefer trawling, to all reachable mobile phones. A suspicious user will probably be suspicious of such a message and will refuse to apply the new settings, but as is the case in mass phishing attacks, it is likely that on big numbers someone will fall for it.
In the case of Samsung terminals, without authenticity checks, it will be sufficient for the victim to accept the settings to be compromised. Slightly more complex is the procedure, in case we want to pierce devices from Huawei, LG or Sony, where the attacker is also required to know the IMSI of the victim’s phone, a sort of unique identification number introduced with 3G. To obtain the IMSI an attacker must have physical access to the victim’s SIM or convince her to install a malicious app that reads it and sends it to the attacker.
If it is impossible to trace back to the IMSI, it is still possible to proceed with the attack by sending two SMS messages, as specified in the paper describing this attack.
Checkpoint has verified the possibility of exploiting the vulnerability on the following phones (before they were updated to solve the problem) Huawei P10, LG G6, Sony Xperia XZ Premium and the Samsung Galaxy series, including S9. We advise immediately to update the device, if the manufacturer has published a patch, and in general not to trust SMS that require a change of settings.