HeroRat, New malware spreads on Android via Telegram
According to the ESET researchers, there is a new malware in circulation that spreads exploiting Telegram. It’s called HeroRat and can be avoided by using common sense.
ESET researchers were the first to put attention to HeroRat: it is a new family of RAT (Remote Administration Tool) for Android that abuses the Telegram protocol since August 2017 and whose source code is available for free since March. With this type of malware it is possible to spy or extract files from infected devices, intercept messages, get contacts, make calls, record audio, detect the position over time, check the settings.
HeroRat is one of the variants of malware and is offered for sale on a dedicated Telegram channel and may have been created from the source code leaked in recent months or may even be the original version of the software.
How does HeroRat work?
Cybercriminals can use different techniques to spread HeroRat, such as through counterfeit apps downloaded from third-party stores. The good news is that the malware is not present on Google Play and is currently distributed mainly in Iran thanks to an app that promotes Bitcoin and free internet connections, as well as additional followers on social media. HeroRat works on all versions of Android once the user offers the required permissions.
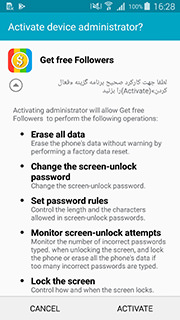 Once installed, the malware launches a small pop-up stating that the app cannot be run and will be uninstalled, with the icon disappearing from the terminal. In reality, this is the moment when the attacker gains control of the terminal through a bot, configured and managed through the Telegram app. Unlike other similarly popular RAT written in the Android Java standard, HeroRat is developed from scratch in C# using Xamarin.
Once installed, the malware launches a small pop-up stating that the app cannot be run and will be uninstalled, with the icon disappearing from the terminal. In reality, this is the moment when the attacker gains control of the terminal through a bot, configured and managed through the Telegram app. Unlike other similarly popular RAT written in the Android Java standard, HeroRat is developed from scratch in C# using Xamarin.
How to defend yourself from HeroRat
ESET naturally recommends its own anti-virus suite for Android in order to defend itself against malware (it is recognized as Android/Spy.Agent.AMS and Android/Agent.AQO), it is advisable to avoid it at birth. The advice is always the same: do not download the app if not from the Google Play Store, and avoid any sources on which you do not place the maximum trust, such as stores that offer counterfeit software or dubious origins.

