VPNFilter: Malware for routers that intercepts data and destroys the device
Discovered by Cisco researchers, the malware is highly sophisticated and can allow attackers to render the device unusable and to perform other criminal actions.
An unidentified group of hackers, but presumably supported by an advanced nation, have compromised over 500 thousand consumer and small-office routers with highly sophisticated malware that can be used to intercept communications, launch attacks on others, and permanently destroy devices with a single command. Cisco researchers took care of this by publishing a detailed report.
The Cisco report was released just over a month after the alarm launched by the US national security department, the FBI and the UK National Cyber Securities Center when they jointly observed that hackers allegedly in the pay of the Russian government were involved in activity of compromising a large number of network devices owned by governments, companies and suppliers of critical infrastructures.
Infections have been found in at least 54 countries that have started growing slowly since 2016. Cisco researchers have been monitoring them for several months, experiencing significant growth in compromise over the past three weeks, which also includes two major attacks on localized devices in Ukraine. The peak, combined with the advanced malware capabilities we’ll discuss a little further, has prompted Cisco to release the report before it was complete.
Cisco notes that VPNfilter – the new malware was baptized – contains a piece of identical code already identified in malware known as BlackEnergy, the latter used in various attacks related to the Russian government, including the famous attack on power grids Ukrainian. The name of Russia is not clearly spelled out in the report.
It should be noted that BlackEnergy has also been used by other attack groups, so the partial overlap of code is not a proof that the VPNFilter was developed under the Russian government’s mandate. The Cisco report did not provide additional attributions to the attacks, noting only that it uses a specific IP address and two domains, one of which the FBI has already seized the servers.
” We have established with confidence that this malware was used to create an extensive infrastructure, difficult to attribute, that can be used for the various operational needs of the threat actor, since the affected devices are legitimately owned by companies or individuals, any malicious activity conducted by infected devices can be mistakenly attributed to those who are actually the victim of the threat actor. The functionalities of the various operating stages and malware plug-ins are extremely versatile and would allow actor to take advantage of the devices in different ways ” explains Cisco researcher William Largent.
VPNFilter – The three operational stages
The aspect on which, there are no doubts is the fact that VPNFilter was developed by a group with advanced skills. The first stage of malware operation includes the compromise of devices with firmware based on Busybox and Linux and is compiled for various CPU architectures.
The main purpose is to identify a server controlled by the attackers so as to move on to the second operational stage, with more advanced features. The server is detected by downloading an image from photobucket.com and extracting an IP address from six integer values used for GPS coordinates and stored in the EXIF field.
In case you can not download the file from Photobucket, the malware tries to download the image from toknowall * DOT * com. In the event that this attempt is not successful, a ” listener ” is opened that awaits specific packet-triggers sent by the attacker. The listener controls the public ip from api-ipify * DOT * org and stores them for later use. This phase persists even after the infected device is restarted.
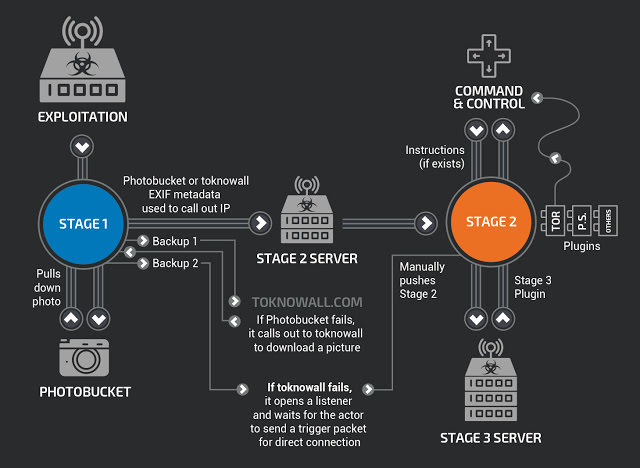 The second stage of operation involves activities of real intelligence, with the collection of files, the execution of commands, the recovery of information and the management of the device. It is at this stage that, in some versions of the malware, a ” self-destruction “ feature can be exploited that makes the router unusable by overwriting a key portion of the firmware and rebooting the device. The researchers are convinced that, even without this feature, attackers are able to make the device unusable manually, remotely.
The second stage of operation involves activities of real intelligence, with the collection of files, the execution of commands, the recovery of information and the management of the device. It is at this stage that, in some versions of the malware, a ” self-destruction “ feature can be exploited that makes the router unusable by overwriting a key portion of the firmware and rebooting the device. The researchers are convinced that, even without this feature, attackers are able to make the device unusable manually, remotely.
Then there is a third stage of operation that includes at least two plug-in modules: a packet-sniffer capable of intercepting all the traffic passing through the device and a module for communications obscured by Tor. According to the researchers at this stage, it is possible that other plug-ins not yet discovered will operate.
What devices are affected?
VPNFilter malware affects various Linksys, MikroTik, Netgear and TP-Link consumer routers as well as some QNAP NAS devices. It is one of the few malware that affects network / Internet-of-Things devices that can survive a device reboot. Symantec published a note in which it lists a number of devices targeted by VPNFilter, although it is not known if there may be other affected devices:
- Linksys : E1200, E2500, WRVS4400N
- Netgear : DGN2200, R6400, R7000, R8000, WNR1000, WNR2000
- TP-Link : R600VPN
- MikoTik : RouterOS for Cloud Core Routers – versions 1016, 1036 and 1072
- QNAP : TS251, TS439 Pro, NAS with QTS software
Researchers have not yet identified how devices are infected, although most of those targeted are also subject to exploits that are already publicly known or are protected by default credentials, making compromise simple enough.
How to run for cover
Cisco and Symantec warn those in possession of any of these devices to perform a factory reset, a process that typically requires the pressure of a specific button located on the back of the device (often to be done with a pointed object) for ten seconds. This operation also eliminates the configuration of the device, which will obviously be reconfigured once it is restarted.
A simple restart of the device will have in any case the effect of stopping at least the operation of steps 2 and 3 unless until phase 1 will provide to reinstall the necessary components. Users should also change all default passwords, ensure that their devices are equipped with the latest firmware and when possible, disable remote administration.
There is currently no easy way to determine if a router has been compromised or not. It is still unclear whether the latest version of the firmware and non-default passwords may have prevented the infection. Although, as mentioned, attackers have used known vulnerabilities, it is good to keep in mind that, given the generally low quality of the firmware of the network / IoT devices, it is possible that zero-day leaks are also exploited that manufacturers are not aware.

