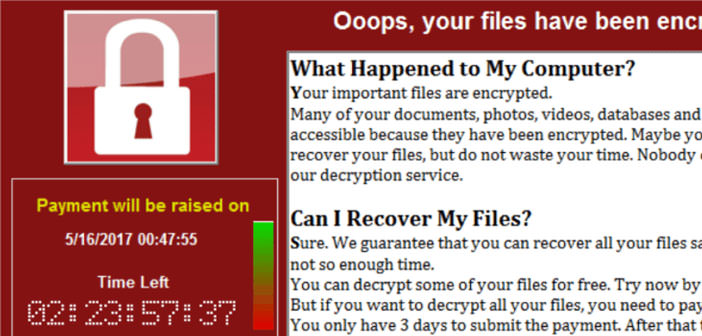
It has the name Wanna Decrypter but in these hours, it’s best known as WannaCry, I wanna cry, the new ransomware that yesterday’s featured the discussions on the web and is spreading like a problem we have unfortunately already seen in the past with other episodes of this type.
Ransomware blocks the system on which it was installed, making it impossible to use and blocking access to saved data until an unlocking process based on a payment is triggered. By analogy, we could say that this is a ransom with ransom, all that happens in a digital context. The amount initially was $300, to be sent with the equivalent in Bitcoin, but some reports indicate that the figure has in the meantime increased to$ 600.
Once the system is infected, the ransomware installs a series of programs, adding it to the Windows registry so that it is always active at each restart of the machine. Inflicts data, also involving associated storage devices such as external hard drives and USB flash drives; It also takes action on the operating system image volumes previously created, blocking access to system repair utilities. It makes the system completely unusable by requiring the user a sum of money to unlock and resume possession.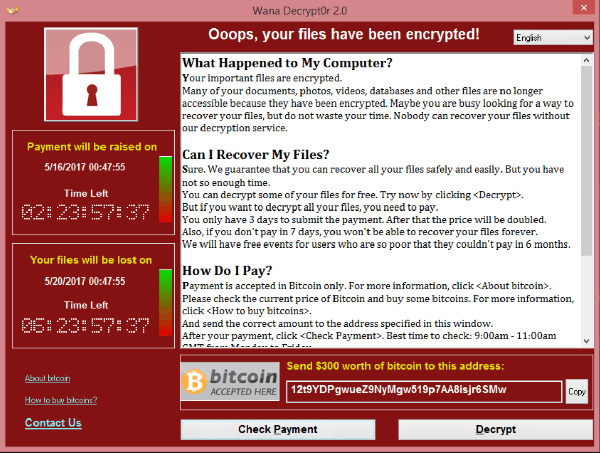 The heart of this attack is the exploitation of a flaw in the Smb Server of the Windows operating system, highlighted by Microsoft and updated with its security update released in March. The spread of this new ransomware has been greatly facilitated by the connection to the web of many systems that are not constantly kept up-to-date and do not integrate fixes to security issues that may occur periodically. At present, there is no specific data about it but it is not difficult to imagine that many of the infected systems are based on Windows XP operating system, still very popular in public environments and, which is no longer supported with Microsoft’s security patches for more than a year.
The heart of this attack is the exploitation of a flaw in the Smb Server of the Windows operating system, highlighted by Microsoft and updated with its security update released in March. The spread of this new ransomware has been greatly facilitated by the connection to the web of many systems that are not constantly kept up-to-date and do not integrate fixes to security issues that may occur periodically. At present, there is no specific data about it but it is not difficult to imagine that many of the infected systems are based on Windows XP operating system, still very popular in public environments and, which is no longer supported with Microsoft’s security patches for more than a year.
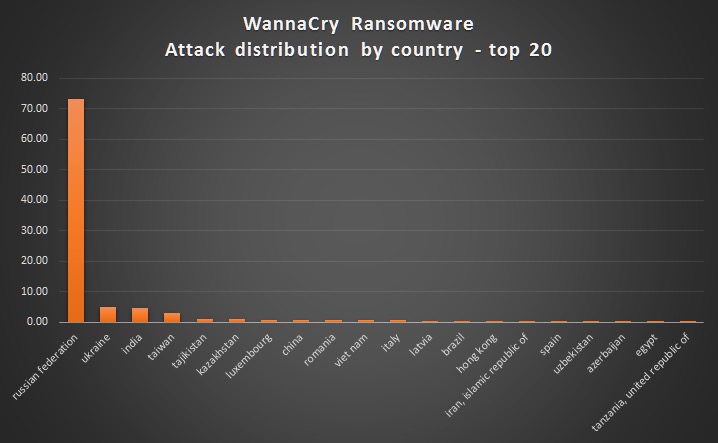
Ransomware initially spread to Spain and Britain, affecting mostly PCs used in work environments and public places. Significant, for example, that in Britain was proliferated within the hospitals, greatly diminishing its operations by having it bundled computer systems. It has also spread to Italy, although the number of attacks detected is circumscribed.
WannaCry is based on the two EternalBlue, and DoublePulsar exploits, coming from a variety of NSA-owned utilities that have been hacked into the hands of recently. The exploits have long been active but only in March they were locked by operating system with an update released by Microsoft for operating systems that are currently covered by security updates.
We recommend that you verify that you have updated your Windows operating system with the various security patches and updates that your company has released, and if you install the patch specific to this address from the Microsoft site. The advice, often given for granted but which is good to remember, is always valid, to use an antivirus on its updated system.